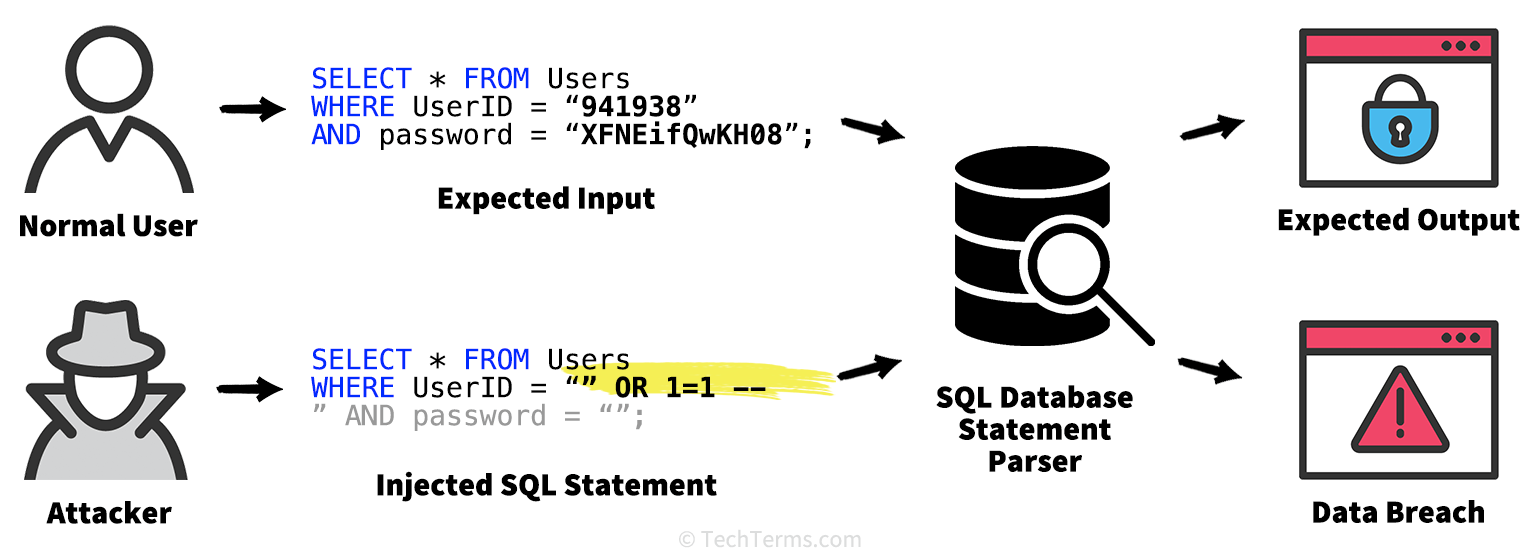
Sql Injection Get Data From Another Table . The first steps are identical to the labs sql injection union attack,. sql injection using union. when an application is vulnerable to sql injection, and the results of the query are returned within the application's. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. sql injection vulnerabilities are actually not that difficult to find, imho. The simple rule to obey is this: The results from the query are returned in. this lab contains a sql injection vulnerability in the product category filter. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other.
from techterms.com
The results from the query are returned in. The first steps are identical to the labs sql injection union attack,. sql injection vulnerabilities are actually not that difficult to find, imho. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The simple rule to obey is this: sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. when an application is vulnerable to sql injection, and the results of the query are returned within the application's. sql injection using union. this lab contains a sql injection vulnerability in the product category filter.
SQL Injection Definition
Sql Injection Get Data From Another Table sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. sql injection vulnerabilities are actually not that difficult to find, imho. when an application is vulnerable to sql injection, and the results of the query are returned within the application's. The results from the query are returned in. The simple rule to obey is this: this lab contains a sql injection vulnerability in the product category filter. The first steps are identical to the labs sql injection union attack,. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. sql injection using union.
From thehackerish.com
SQL injection examples for practice thehackerish Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. The results from the query are returned. Sql Injection Get Data From Another Table.
From javabypatel.blogspot.com
SQL Injection attack example in Java. JavaByPatel Data structures Sql Injection Get Data From Another Table The results from the query are returned in. sql injection vulnerabilities are actually not that difficult to find, imho. sql injection using union. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. in cases where the application responds with the. Sql Injection Get Data From Another Table.
From whatismyipaddress.com
SQL Injection What It Is and How Does It Work Sql Injection Get Data From Another Table sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. The simple rule to obey is this: when an application is vulnerable to sql injection, and the results of the query are returned within the application's. this lab contains a sql injection. Sql Injection Get Data From Another Table.
From www.geeksforgeeks.org
Basic SQL Injection and Mitigation with Example Sql Injection Get Data From Another Table The simple rule to obey is this: sql injection vulnerabilities are actually not that difficult to find, imho. The first steps are identical to the labs sql injection union attack,. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The results. Sql Injection Get Data From Another Table.
From hacklendikriptokoin.blogspot.com
Sql injection Tutorials Beginners Guide website hacking Hacklendi Sql Injection Get Data From Another Table this lab contains a sql injection vulnerability in the product category filter. The simple rule to obey is this: sql injection vulnerabilities are actually not that difficult to find, imho. sql injection using union. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to. Sql Injection Get Data From Another Table.
From techtricktips.blogspot.com
SQL Injectioni Cheat Sheet Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. this lab contains a sql injection. Sql Injection Get Data From Another Table.
From www.hackguide4u.com
Sql Injection Presentation Transcript Learn Cyber Security Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The first steps are identical to the labs sql injection union attack,. The results from the query are returned in. sql injection using union. sql injection is a type of vulnerability. Sql Injection Get Data From Another Table.
From www.one.com
What is SQL injection, and how to prevent SQL injection attacks? Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The first steps are identical to the labs sql injection union attack,. The results from the query are returned in. this lab contains a sql injection vulnerability in the product category filter.. Sql Injection Get Data From Another Table.
From www.vaadata.com
SQLi principles, impacts and security best practices Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The results from the query are returned in. sql injection vulnerabilities are actually not that difficult to find, imho. The first steps are identical to the labs sql injection union attack,. . Sql Injection Get Data From Another Table.
From www.slideshare.net
SQL Injection Attacks Sql Injection Get Data From Another Table sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. The results from the query are returned in. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from. Sql Injection Get Data From Another Table.
From fakecineaste.blogspot.com
fakecineaste SQL Injection Vulnerability Sql Injection Get Data From Another Table sql injection using union. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The results from the query are returned in. this lab contains a sql injection vulnerability in the product category filter. The first steps are identical to the. Sql Injection Get Data From Another Table.
From www.wikihow.com
How to Prevent SQL Injection in PHP (with Pictures) wikiHow Sql Injection Get Data From Another Table sql injection using union. The results from the query are returned in. sql injection vulnerabilities are actually not that difficult to find, imho. when an application is vulnerable to sql injection, and the results of the query are returned within the application's. The first steps are identical to the labs sql injection union attack,. sql injection. Sql Injection Get Data From Another Table.
From www.qafox.com
SQL Injection Payload Two Part 4 QAFox Sql Injection Get Data From Another Table when an application is vulnerable to sql injection, and the results of the query are returned within the application's. The first steps are identical to the labs sql injection union attack,. The results from the query are returned in. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or. Sql Injection Get Data From Another Table.
From binary-studio.com
Understanding SQL Injections and Securing Your Application Binary Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. The simple rule to obey is this: sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query.. Sql Injection Get Data From Another Table.
From blueteamresources.in
Prevent SQL Injection Attacks 7Step Investigation Guide Sql Injection Get Data From Another Table in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. sql injection vulnerabilities are actually not that difficult to find, imho. sql injection using union. The results from the query are returned in. sql injection is a type of vulnerability. Sql Injection Get Data From Another Table.
From www.thesecuritybuddy.com
What is the SQL injection attack? The Security Buddy Sql Injection Get Data From Another Table sql injection vulnerabilities are actually not that difficult to find, imho. this lab contains a sql injection vulnerability in the product category filter. sql injection is a type of vulnerability that occurs in an application's database when an attacker can insert or inject sql commands into a query. The first steps are identical to the labs sql. Sql Injection Get Data From Another Table.
From widehostmedia.com
Mengenal Apa itu SQL Injection Wide Host Media Sql Injection Get Data From Another Table The simple rule to obey is this: this lab contains a sql injection vulnerability in the product category filter. The results from the query are returned in. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. sql injection using union.. Sql Injection Get Data From Another Table.
From www.theknowledgeacademy.com
SQL Injection in Cyber Security A Brief Guide Sql Injection Get Data From Another Table sql injection using union. in cases where the application responds with the results of a sql query, an attacker can use a sql injection vulnerability to retrieve data from other. sql injection vulnerabilities are actually not that difficult to find, imho. sql injection is a type of vulnerability that occurs in an application's database when an. Sql Injection Get Data From Another Table.